Healthcare software handles some of the most sensitive data in existence. Patient medical histories, treatment plans, and personal identifiers flow through these systems every day. One breach can expose thousands of records, destroy patient trust, and trigger massive regulatory penalties.
And these breaches are happening often. As of January 28, 2025, the U.S. Office for Civil Rights (OCR) reported 725 healthcare data breaches involving 500 or more records in 2024 alone. That marks the third consecutive year with over 700 large-scale breaches, a clear indication that the industry is under constant pressure from cyber threats.
At the same time, regulations such as HIPAA in the U.S. and GDPR in Europe establish strict standards for handling patient data. Failing to comply isn’t just a technical issue. It’s a legal and financial risk.
So what does it take to build software that protects patient data and meets regulatory expectations?
You need:
- A working knowledge of current healthcare regulations and how they apply to your software
- A security-first development approach that considers risks from day one
- And a commitment to maintaining compliance as your software evolves
In this guide, we’ll walk you through what compliance and security really look like in a healthcare software context, covering key regulations, best practices, and actionable steps to help you safeguard both your users and your platform.
Key Takeaways
- Healthcare software must comply with multiple regulations, including HIPAA, GDPR, HITECH, and FDA guidelines, each with specific requirements for data protection.
- Security measures go beyond encryption to include access controls, audit trails, regular risk assessments, and incident response planning.
- Cloud environments introduce unique compliance challenges that require specialized expertise and continuous monitoring.
- Modern threats demand advanced solutions like AI-powered threat detection and managed detection and response (MDR) services.
- Pi Tech's Specless Engineering methodology builds compliance into healthcare software from day one, reducing risk while accelerating development.
Why Compliance and Security Matter in Healthcare Software
Healthcare organizations face a perfect storm of challenges. Cyberattacks target medical facilities because health records sell for 10-50 times more than credit card numbers on the dark web.
At the same time, regulatory bodies impose strict requirements with severe penalties for violations.
Consider what happened when a major medical billing company suffered a ransomware attack. In February 2024, Change Healthcare, a major medical billing and healthcare payment processing company owned by UnitedHealth Group, suffered a ransomware attack that paralyzed its systems, disrupting nationwide billing and insurance claims processing.
The breach paralyzed cash flow for organizations representing 20% of the U.S. economy. Hundreds of medical practices nearly went bankrupt. Patient care stopped at facilities across the country.
This wasn't an isolated incident. Healthcare breaches happen constantly through various attack vectors:

Each breach damages more than systems. Patients lose trust when their personal health information gets exposed. Care delivery stops when systems go offline. Organizations face investigations, lawsuits, and penalties that can reach millions of dollars.
Core Healthcare Regulations You Must Follow
Healthcare software operates under multiple regulatory frameworks. Each has specific requirements that shape how you design, build, and maintain your systems.
Understanding these regulations forms the foundation of any compliant healthcare software strategy.
HIPAA: The Foundation of Healthcare Compliance
The Health Insurance Portability and Accountability Act (HIPAA) is the backbone of healthcare data protection in the United States. It sets strict rules for how health information should be accessed, stored, shared, and secured.
HIPAA has three main components you’ll need to build around:
The Privacy Rule controls how organizations use and disclose protected health information (PHI). Every use and disclosure must have a valid purpose. Patient care, payment processing, and healthcare operations represent the primary permitted uses. Beyond these, you typically need explicit patient authorization. The rule also grants patients specific rights: accessing their records, requesting corrections, and receiving accountings of disclosures.
The Security Rule takes a different approach. Rather than prescribing exact technical solutions, it requires organizations to implement reasonable and appropriate safeguards for electronic PHI. This flexibility allows organizations to scale security measures to their size and complexity. However, certain safeguards remain mandatory for everyone:

The Breach Notification Rule creates a strict timeline for responding to security incidents. Organizations have 60 days from discovery to notify affected individuals. Breaches affecting 500 or more people trigger additional requirements: immediate notification to HHS and prominent media outlets in the affected area.
HIPAA penalties reflect the seriousness of violations:
- Tier 1: Unknown violations despite reasonable diligence ($100-$50,000 per violation)
- Tier 2: Violations due to reasonable cause ($1,000-$50,000 per violation)
- Tier 3: Violations from willful neglect, corrected within 30 days ($10,000-$50,000 per violation)
- Tier 4: Violations from willful neglect, not corrected ($50,000-$2 million per violation)
GDPR: Global Data Protection Standards
If your healthcare software processes data from EU citizens, you’re legally required to follow the General Data Protection Regulation (GDPR), no matter where your organization is based. This law isn’t just for European companies. It applies globally.
Unlike HIPAA, which focuses on permitted uses and minimum safeguards, GDPR centers on individual rights and your accountability as an organization. It expects you to justify every piece of data you collect and every way you use it.
GDPR gives individuals eight core rights over their personal data. A few of the most important for healthcare software include:
- Right to Access: Patients can request and receive a copy of every piece of data you hold about them.
- Right to Rectification: They can ask you to correct inaccurate or outdated information.
- Right to Erasure ("right to be forgotten"): In some cases, individuals can request that their data be deleted.
That last one—erasure—can be tricky in healthcare. You can’t just delete medical records on request, since legal and clinical obligations often require you to retain them. But even when erasure isn’t allowed, you still need to explain why and document it clearly.
GDPR also requires you to follow “privacy by design and by default”. In plain terms, you need to think about data protection at every stage of development, not bolt it on at the end.
This means:
- Only collecting what’s necessary
- Securing data from the start
- Giving users control over how their data is handled
Because healthcare software typically processes large volumes of sensitive health data, you're expected to conduct a Data Protection Impact Assessment (DPIA) before deploying or updating any major features.
A DPIA should clearly outline:
- Why you're collecting and processing data
- The risks to patients' rights and freedoms
- The steps you're taking to reduce those risks
If your software handles large-scale processing of health data, you'll also need to appoint a Data Protection Officer (DPO). This person:
- Advises your team on data protection obligations
- Acts as your contact point with GDPR authorities
- Must remain independent (they report directly to leadership and can’t be penalized for doing their job)
Together, these GDPR requirements push you to treat data protection as a core part of your development process, not just a legal checkbox.
HITECH: Strengthening Electronic Health Records Security
The Health Information Technology for Economic and Clinical Health (HITECH) Act didn’t replace HIPAA, but it made it much tougher. Passed in 2009, HITECH recognized that the rise of electronic health records (EHRs) introduced new risks that required stronger protections.
If you’re building or managing healthcare software, HITECH is part of the reason HIPAA enforcement today is stricter, broader, and more complex.
One major change was shifting more responsibility onto third-party vendors. Before HITECH, only covered entities like hospitals or insurers were held liable for HIPAA violations, even when the issue originated from a vendor. HITECH changed that by making business associates directly accountable for how they handle protected health information (PHI).
That means if you’re offering any service that processes, stores, or transmits PHI on behalf of a healthcare provider, you’re legally on the hook for staying compliant. This includes:
- Cloud hosting providers
- EHR and patient management platforms
- Medical billing services
- Third-party data storage or backup vendors
- Analytics and reporting tools that access PHI
You can’t rely on your client’s HIPAA program to cover your responsibilities. You're expected to have your own internal policies, safeguards, and breach response processes.
HITECH also introduced a tiered penalty structure to reflect the severity and intent behind violations better. Minor, unintentional breaches are treated differently from willful neglect, but all can carry serious financial consequences. And instead of leaving enforcement solely to federal agencies, HITECH gave state attorneys general the power to take action against violators. That increased the likelihood of penalties being pursued, even for smaller breaches.
Another part of HITECH was its push to digitize healthcare records through “meaningful use” incentives. These programs offered financial rewards to providers who adopted certified EHR systems and used them effectively. But the goal wasn’t just digitization—it was secure and responsible digitization.
As a result, organizations accepting these incentives were also expected to put proper safeguards in place. That includes everything from audit trails and access controls to encryption and regular risk assessments. For software developers, it meant a clear message: build systems that protect patient data by design.
If your platform interacts with EHRs in any way, the expectations set by HITECH still apply today. You're not just supporting healthcare. You’re helping secure it.
FDA Regulations for Medical Software
Software that qualifies as a medical device faces additional regulatory requirements from the FDA. Not all healthcare software falls under FDA jurisdiction, but the boundaries continue evolving as software capabilities expand.
The FDA uses a risk-based approach to regulate medical device software:

21 CFR Part 11 establishes requirements for electronic records and signatures in FDA-regulated environments. Compliance demands:
- Validation of systems to ensure accuracy and reliability
- Secure, computer-generated, time-stamped audit trails
- Limited system access to authorized individuals
- Use of secure electronic signatures
- Ability to generate accurate and complete copies of records
Medical Device Reporting (MDR) regulations require manufacturers to report adverse events and product problems. Healthcare software companies must establish procedures to identify, evaluate, and report events that could cause serious injury or death.
The Quality System Regulation (QSR) mandates comprehensive quality management systems. Software development must follow defined procedures including design controls, validation protocols, and change management processes.
Building Security Into Healthcare Software
Effective security in healthcare software goes beyond implementing technical controls. It requires a comprehensive approach that addresses people, processes, and technology throughout the software lifecycle.
Risk Assessment: The Foundation of Security Planning
Every security program starts with understanding your risks. Healthcare organizations must conduct regular risk assessments to identify vulnerabilities before attackers exploit them. The process follows a structured approach:
Step 1: Create an Asset Inventory
Document all systems, applications, and data repositories that handle PHI. Include details about data flows, access points, and dependencies. Many organizations discover forgotten systems or shadow IT during this process.
Step 2: Identify Threats and Vulnerabilities
Examine each asset for potential weaknesses. Common vulnerabilities in healthcare software include:
- Unpatched systems running outdated software
- Weak authentication mechanisms
- Excessive user permissions
- Unencrypted data transmission
- Poor logging and monitoring
Step 3: Assess Impact and Likelihood
Not all risks deserve equal attention. Evaluate each vulnerability based on:
- Potential impact on patient care
- Financial consequences of exploitation
- Likelihood of occurrence based on threat intelligence
- Existing controls that might mitigate the risk
Step 4: Develop Remediation Plans
Create specific action plans to address high-priority risks. Assign ownership, set deadlines, and allocate resources. Track progress through regular reviews.
Implementing Technical Safeguards
Technical safeguards are the backbone of healthcare software security. These controls don’t just check a compliance box. They actively protect sensitive data and help prevent breaches. While the specifics may vary depending on how your system is built, there are a few safeguards that every implementation should include, no matter the size or complexity of your platform.
The goal is to create a layered defense: encrypt data, limit who can access it, and keep a close eye on everything happening in your system.
Let’s break it down.
Encryption Standards
Encryption is non-negotiable. If your software handles PHI, you need to protect it both while it’s stored and while it’s moving between systems.
For data at rest, use:
- AES-256 encryption as the baseline standard
- Proper key management. Use hardware security modules (HSMs) or cloud-based key management services
- Separate storage for keys. Never store encryption keys on the same system as the encrypted data
For data in transit, enforce TLS 1.2 or higher across all communication channels. This includes:
- Web traffic (HTTPS)
- API calls
- Database connections
- Third-party service integrations
- Emails containing PHI
Access Control Architecture
Access control is another critical layer. It’s not enough to encrypt data if anyone can log in and access everything. You need to build strict controls around who can access what and how.
Start with multi-factor authentication (MFA). Passwords alone are too easy to compromise, especially in healthcare environments where user accounts often have broad access. Choose the MFA method based on the level of access and user convenience:

Role-based access control (RBAC) ensures users only access data necessary for their jobs. Define roles based on job functions rather than individuals. Common healthcare roles include:
- Clinical staff (doctors, nurses, therapists)
- Administrative personnel (billing, scheduling)
- Technical staff (IT, system administrators)
- Business associates (external vendors, consultants)
Implement the principle of least privilege rigorously. Users should have the minimum access required to perform their duties. This limits damage from both external attacks and insider threats.
Audit Logging and Monitoring
Even the best access controls need visibility behind them. That’s where audit logging and monitoring come in.
Your software should log key activities that affect PHI and system security, such as:
- Every access attempt (both successful and failed)
- Changes to user roles and permissions
- Configuration updates to critical systems
- Data exports, downloads, or backups
- Any administrative or high-privilege actions
These logs become a vital part of your breach detection and compliance strategy—but they’re also sensitive. Treat them like valuable data. That means:
- Storing logs separately from your production environment
- Making them tamper-proof so no one can silently erase or alter them
- Retaining them for at least six years, as required by HIPAA and other regulations
To take it further, integrate your logs with real-time monitoring systems. A modern Security Information and Event Management (SIEM) platform can help you catch problems as they happen by flagging suspicious patterns like:
- Repeated failed login attempts
- Access from unfamiliar or high-risk locations
- Sudden spikes in data exports
- Attempts to elevate user privileges
- Activity that matches known attack signatures
The goal isn’t just to collect logs. It’s to use them as a defense system. With good monitoring in place, you’re not just responding to security incidents after the fact. You’re spotting them early and stopping them before they escalate.
Application Security Throughout Development
Security cannot be an afterthought in healthcare software development. The stakes are too high, and retrofitting security into completed applications proves expensive and ineffective.
Instead, integrate security practices throughout the development lifecycle.
Start by using secure design principles. Threat modeling is a good first step. It helps you identify how attackers might try to compromise your system before any code is written. In healthcare applications, some of the most common threats include:
- SQL Injection Attacks: These target your database through manipulated queries. Use parameterized queries or stored procedures to prevent them. Avoid string concatenation with user input.
- Cross-Site Scripting (XSS): Attackers inject malicious scripts into web apps. Apply content security policies (CSP), validate all input, and properly encode output based on context.
- Authentication Bypass: Weak login and session mechanisms can let unauthorized users in. Use strong session controls, enable account lockouts after repeated failures, and secure your password reset flows.
Once your design is solid, secure coding practices help reduce risk at the implementation level.
Developers need proper training to understand not just how to build features, but how to build them safely.
Focus on these key areas:
- Input Validation. All external data must be validated:
- Enforce correct data types and formats
- Set reasonable length limits
- Use allowlists (e.g., accepted values), not blocklists
- Validate on both the client and server side
- Enforce correct data types and formats
- Error Handling. In healthcare, even error messages can become a liability. Don’t expose stack traces or internal logic in user-facing errors. Show general messages to users while logging detailed errors internally for debugging.
- Dependency Management. Most applications use third-party libraries, which means you inherit their risks too. Maintain an up-to-date inventory of dependencies, monitor them for security updates, and regularly scan for known vulnerabilities using automated tools.
Once the code is in place, testing becomes the next defense layer—and it can’t just be functional testing. Security testing needs to happen continuously, not just at the end.
Include these types of testing in your process:
- Static Application Security Testing (SAST): This scans your source code for vulnerabilities without running the app. Integrate SAST tools into your CI/CD pipeline to catch issues early, such as:
- Hard-coded credentials
- Unsafe cryptographic functions
- Insecure function calls
- Information disclosure via logs or debug messages
- Hard-coded credentials
- Dynamic Application Security Testing (DAST): Unlike SAST, DAST tests your application while it's running. It simulates attacks to identify vulnerabilities like:
- Broken authentication
- Session handling issues
- Injection flaws
- Misconfigured headers or permissions
- Broken authentication
- Penetration testing: Automated tools can only go so far. Hire professionals to test your app from an attacker’s perspective. They can combine smaller issues into bigger threats and uncover logic flaws that tools miss. Plan to do this:
- Before every major release
- After big changes to your architecture
- At least once a year for high-risk systems
- Anytime a breach or major incident occurs
- Before every major release
Security doesn’t just belong to one phase or one team. It has to be a continuous, shared responsibility throughout your development process. When done right, it not only protects patient data, it builds trust into every part of your application.
Cloud Security Considerations for Healthcare
Cloud adoption in healthcare continues to accelerate annually, driven by the need for scalability, cost considerations, and enhanced collaboration capabilities. However, cloud environments introduce unique compliance challenges that many healthcare organizations underestimate.
Shared Responsibility Models
Cloud security operates on a shared responsibility model. The exact division varies by service type:
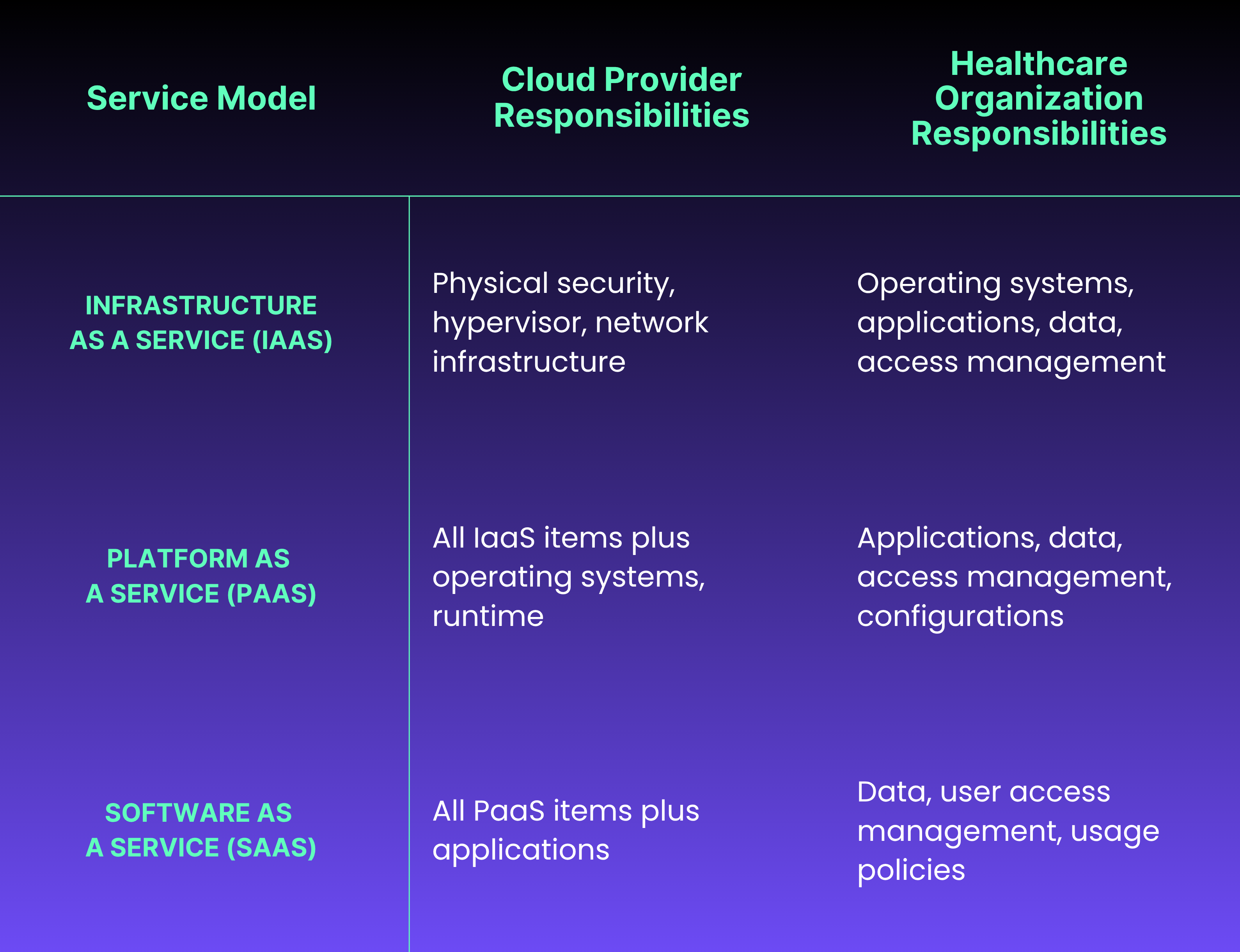
This model creates confusion when organizations assume cloud providers handle more security than they actually do. For example, AWS provides tools for encryption, but organizations must enable and configure them properly. Misconfigurations remain the leading cause of cloud data breaches in healthcare.
Cloud-Specific Compliance Requirements
HIPAA requires Business Associate Agreements (BAAs) with cloud providers handling PHI. Not all cloud services qualify for BAAs. Organizations must verify BAA eligibility before using any cloud service for PHI. Major providers like AWS, Azure, and Google Cloud offer BAAs but only for specific services within their platforms.
Data residency becomes complex in cloud environments. Healthcare data may replicate across multiple data centers for availability. Some regulations require data to remain within specific geographic boundaries. Organizations must:
- Understand where cloud providers store and process data
- Configure services to meet residency requirements
- Monitor for unauthorized data movement
- Maintain documentation for compliance audits
Securing Healthcare Workloads in the Cloud
Start with a strong foundation through proper identity and access management (IAM). Cloud IAM differs significantly from traditional on-premises approaches:
Service Accounts and Roles Applications need identities too. Create specific service accounts for each application component. Grant only necessary permissions through role-based policies. Rotate credentials regularly using automated tools.
Federated Identity Connect cloud identity systems with existing organizational directories. This enables single sign-on while maintaining centralized control. Configure SAML or OIDC integration carefully to prevent unauthorized access.
Privileged Access Management Administrative access to cloud resources requires extra protection. Implement:
- Just-in-time access that grants temporary elevated privileges
- Approval workflows for sensitive operations
- Session recording for forensic analysis
- Regular access reviews to remove unnecessary permissions
Network security in cloud environments requires rethinking traditional perimeter-based approaches. Implement zero-trust principles:
Microsegmentation divides networks into small zones with specific security policies. Healthcare applications benefit from separating:
- Web tiers from application tiers
- Application tiers from database tiers
- Production from non-production environments
- PHI-processing systems from general workloads
Virtual private clouds (VPCs) provide network isolation. Design VPC architectures that:
- Minimize internet-facing surfaces
- Use private subnets for sensitive resources
- Implement network access control lists (ACLs)
- Monitor traffic with flow logs
Data Protection in Cloud Storage
Cloud storage gives you scalability and flexibility, but in healthcare, it also introduces new responsibilities. Patient data stored in the cloud still falls under strict privacy and security regulations. That means it’s up to you to configure your cloud environment properly, not just rely on what the provider offers by default.
The first step is getting encryption right. Most cloud platforms offer encryption tools, but how you use them matters.
Make sure encryption is enabled for all storage services. Depending on your cloud provider, you typically have a few options for encrypting data at rest:
- Server-Side Encryption (SSE): The provider encrypts the data for you after it’s uploaded:
- Provider-managed keys. Easiest to implement, but you give up some control
- Customer-managed keys. Stored in your own key management system (KMS), giving you more visibility and control
- Customer-provided keys. You handle the keys entirely, which offers full control but adds complexity
- Provider-managed keys. Easiest to implement, but you give up some control
- Client-Side Encryption: You encrypt the data before it ever leaves your system. This means the cloud provider never sees the raw data, even in memory. It adds an extra layer of protection but also:
- Makes key management more complex
- Can interfere with search and analytics features, since the provider can’t inspect the data
- Makes key management more complex
Once encryption is in place, access controls are your next line of defense. Many breaches happen not because the data was unprotected, but because access was misconfigured.
Be careful with how you set up permissions and policies. Avoid these common mistakes:
- Setting overly permissive policies that allow public access to storage buckets
- Skipping access logging, which leaves you blind to who accessed what
- Ignoring lifecycle policies, which can result in old or unnecessary data being left unprotected
- Forgetting versioning, which can be critical for both compliance and recovery
Finally, you need visibility into what’s happening in your cloud environment. That means auditing every interaction with your data.
Enable your cloud provider’s native auditing tools. These services give you real-time logs that help track data activity and detect suspicious behavior. Depending on your platform, look for:
- AWS CloudTrail
- Azure Monitor and Activity Logs
- Google Cloud Audit Logs
These tools typically offer:
- Detailed records of every API call and configuration change
- Patterns of who accessed what, and when
- Alerts for failed access attempts or unusual activity
Auditing doesn’t just help with security. It’s also critical for proving compliance during regulatory reviews.
When configured properly, cloud storage can meet and even exceed on-premises security standards. However, it requires careful planning, strict controls, and ongoing oversight.
Modern Threats and Advanced Protection Strategies
The threat landscape for healthcare software is constantly evolving. Attackers develop new techniques while defenders race to keep up. Understanding current threats helps organizations prepare appropriate defenses.
1. Emerging Threat Vectors
One of the most aggressive and damaging threats right now is ransomware. Healthcare organizations are frequent targets because attackers know you’re more likely to pay to restore critical systems like patient records, scheduling, and lab results.
Modern ransomware campaigns typically follow a well-defined pattern:
- Initial access is gained through phishing emails, exposed remote access tools, or unpatched systems
- Attackers establish persistence, often using built-in system tools to stay under the radar
- Lateral movement allows them to explore your network and locate high-value systems
- Before launching the ransomware, they exfiltrate sensitive data, setting up “double extortion” threats: pay to restore access and to prevent public data leaks
- Finally, they encrypt files across the network in a coordinated, simultaneous strike
Another major risk is supply chain attacks. These target you indirectly—through vendors, partners, or third-party tools integrated into your systems. The healthcare sector relies heavily on specialized service providers, and attackers take advantage of that.
Recent supply chain attacks have involved:
- Compromised update systems that push out malicious code disguised as official patches
- Injected malware in open-source or vendor libraries
- Stolen credentials from outsourced IT providers or business associates
- Exploitation of vulnerabilities in connected medical devices used in clinical settings
These attacks are especially dangerous because they often come through trusted channels, and many healthcare organizations don’t have the resources to deeply vet every vendor’s security posture.
A newer and growing concern is the use of AI by attackers. While AI helps defenders too, it’s also making some attacks smarter and harder to detect.
Attackers are now using AI to:
- Craft phishing emails that are highly targeted, readable, and free of obvious red flags
- Scan and exploit vulnerabilities faster than humans can
- Mimic normal user behavior to evade detection systems
- Conduct large-scale social engineering, adapting tactics based on how people respond
These techniques allow attackers to scale their operations while remaining stealthy. Traditional firewalls, antivirus, and static rules-based systems struggle to keep up with this level of sophistication.
Staying ahead of these threats requires more than just reacting to incidents. It means rethinking security architecture, continuously assessing vendor risk, training staff to spot early warning signs, and deploying modern defense tools that are built to detect behavior, not just code.
2. Advanced Protection Technologies
Modern threats can’t be stopped with outdated defenses. As attacks become more coordinated and complex, healthcare organizations are turning to advanced technologies that go beyond traditional security tools. These solutions don’t just block threats. They help you understand them, respond faster, and stay ahead of emerging risks.
One major shift is the adoption of Extended Detection and Response (XDR). These platforms consolidate data from across your endpoints, cloud environments, networks, and applications to provide a single, unified view of your security landscape.
XDR tools make a real difference by:
- Detecting multi-stage attacks that unfold across systems
- Automatically isolating infected machines or accounts to stop the spread
- Reducing false positives by adding context to alerts
- Making investigations faster through a centralized dashboard
Some solutions are even built specifically for healthcare. They understand what emergency access to PHI looks like and can tell the difference between urgent care workflows and unauthorized behavior. This helps reduce unnecessary alerts without weakening protection.
Another major advancement is the shift toward Zero Trust Architecture. The idea here is simple: don’t assume anything is safe just because it’s inside your network. Instead, verify every access request, whether it’s coming from inside the hospital or halfway across the world.
To implement this effectively in a healthcare environment, focus on:
- Verifying identity at every access point, not just usernames, but also device health, authentication strength, and session integrity
- Using micro-segmentation to control lateral movement. Just because a user is authenticated doesn’t mean they should reach every system. Restrict access based on roles and resource sensitivity
- Applying dynamic least privilege. Access isn’t static. Adjust permissions based on:
- Who the user is
- The type of device they’re using
- Where they’re connecting from
- The sensitivity of the data being accessed
- Any active threats in the environment
- Who the user is
AI-powered tools are also becoming a vital part of healthcare cybersecurity. These systems don’t replace your security team, but they can help surface threats faster, automate routine responses, and prioritize the most urgent risks.
Here’s how AI contributes across key security functions:

While AI brings huge advantages, it’s not plug-and-play. Keep in mind:
- The quality of training data directly impacts detection accuracy
- Poorly tuned systems can flood your team with false positives
- Adversarial AI can be used by attackers to fool detection models
- Human oversight is still critical, especially in high-stakes healthcare settings
These tools are most effective when used in conjunction with clear processes and skilled staff. Technology doesn’t replace judgment. It supports it. When used effectively, advanced security platforms help you stay one step ahead of attackers, protect patient data, and meet growing compliance demands without overwhelming manual work.
3. Incident Response for Healthcare Organizations
Even with strong security in place, incidents can still happen. The difference between a minor disruption and a full-blown crisis often comes down to how quickly and effectively you respond. For healthcare organizations, response planning needs to go beyond standard IT procedures. You’re not just protecting systems. You’re protecting patient care.
Your incident response plan should be tailored to the realities of a clinical environment. That means focusing on patient safety, regulatory deadlines, and the potential for legal fallout.
Start with clinical continuity. If your systems go down, care delivery can’t simply pause. Build fallback procedures into your response plan so frontline staff can keep working safely during outages.
Include these key elements:
- Downtime workflows for critical systems like EHRs, scheduling, and lab orders
- Paper-based alternatives to continue essential care and documentation
- Communication protocols to keep clinical teams informed during an incident
- Decision trees to guide clinicians on how to prioritize care and patient safety when technology is unavailable
Don’t just write these plans, test them. Tabletop exercises involving clinical staff help reveal what works, what’s missing, and what needs more training. These exercises simulate real-world scenarios and ensure your team is ready before a crisis hits.
Next, prepare for regulatory fallout. Breaches in healthcare often come with strict reporting obligations, and failing to meet them can lead to fines, legal action, and reputational damage.
Make sure you account for:
- HIPAA’s 60-day breach notification rule, starting from the date of discovery. In some cases, law enforcement may allow a delay if public notice would interfere with an investigation. If that happens, document every conversation and decision.
- State-level breach notification laws, which vary widely. Some states require faster notification than HIPAA and have specific rules about how and what to report.
- GDPR’s 72-hour requirement for breaches affecting EU citizens. This short timeline means you’ll need pre-approved messaging templates and a clear escalation path so you’re not scrambling after a breach.
Once a breach is confirmed, how you handle the evidence can shape the outcome of any legal or regulatory follow-up. You need to act quickly but carefully.
Best practices for evidence preservation include:
- Creating forensic images of affected systems before restoring or wiping them
- Preserving log data before automated systems delete or rotate it
- Keeping detailed records of every action taken, with accurate timestamps
- Maintaining a proper chain of custody, especially if legal proceedings are likely
It’s also worth bringing in external forensics experts. They offer deeper technical skills and serve as independent validators of your findings, something that can be critical if regulators or courts get involved later.
The key to effective incident response isn’t just fast action. It’s a thoughtful, coordinated action. You need to balance recovery with regulatory compliance and patient care. A strong plan, tested regularly, helps ensure you’re ready when it counts most.
Building a Culture of Compliance
Technology alone cannot secure healthcare software. Organizations need a culture where every employee understands their role in protecting patient data. Building this culture requires sustained effort across multiple dimensions.
1. Leadership Commitment
Compliance starts at the top. Executive leadership must demonstrate visible commitment through actions:
Resource allocation shows true priorities. Compliance programs need adequate funding for tools, training, and personnel. Underfunded programs inevitably fail when tested by real threats.
Regular communication reinforces importance. Leaders should discuss compliance in company meetings, emails, and strategic planning. Share both successes and lessons learned from incidents.
Accountability drives behavior. Include compliance metrics in performance evaluations. Reward employees who identify security issues or suggest improvements. Address violations consistently regardless of seniority.
2. Comprehensive Training Programs
Generic, one-size-fits-all security training doesn’t work, especially in healthcare. If training feels irrelevant or disconnected from real tasks, people tune it out. To build real awareness, you need training that speaks directly to the roles people hold and the risks they face.
Effective programs don’t just explain rules. They show how those rules apply to the tools, processes, and decisions staff use every day.
That starts with role-based training modules. Different roles interact with protected health information (PHI) in different ways and face different threats. Tailor the content so it's practical and engaging.
Here’s how to focus training by role:
- Clinical staff
- Handling PHI at the bedside or during virtual care
- Keeping mobile devices (phones, tablets) secure
- Recognizing social engineering attempts in clinical settings
- Using secure channels when communicating with patients
- Handling PHI at the bedside or during virtual care
- Administrative staff
- Spotting phishing and email-based threats
- Properly handling, storing, and disposing of documents
- Managing visitor access to sensitive areas
- Preventing billing fraud or identity theft
- Spotting phishing and email-based threats
- IT and technical staff
- Following secure configuration baselines
- Managing and patching system vulnerabilities
- Responding to incidents quickly and consistently
- Securing cloud environments and integrations
- Following secure configuration baselines
One-time training isn’t enough. People forget what they don’t use, and attackers don’t wait for your next annual refresher.
You need continuous reinforcement built into the work environment. That can include:
- Micro-Learning: Send short, focused lessons on current threats. A quick weekly tip tied to recent healthcare incidents is far more effective than an hour-long annual session.
- Simulated Phishing Tests: Start simple, then increase difficulty. The goal isn’t to shame people. It’s to give them practice spotting real threats. Follow each test with feedback that explains what to watch for next time.
- Security Champions: Find employees in each department who care about doing things the right way. Give them deeper training and tools to support their peers. Champions can answer questions, share reminders, and keep security on people’s radar without needing top-down enforcement.
When training is relevant, continuous, and supported by peers, it stops feeling like a compliance task and becomes second nature.
3. Vendor Management
Vendors play a critical role in healthcare operations, but they also introduce serious risk. If a third-party service provider mishandles PHI, your organization is still accountable. That’s why vendor management isn’t just procurement. It’s a core part of your compliance and security strategy.
You need a structured approach to evaluate, monitor, and work with vendors who have access to sensitive data.
Start with a solid due diligence process before any PHI is shared. Don’t rely on promises, ask for proof.
Key areas to evaluate include:
- Security certifications like SOC 2 Type II, HITRUST, or ISO 27001
- Breach history, including how they responded and what changed afterward
- Cyber insurance coverage to understand their financial preparedness
- References from other healthcare organizations, preferably with similar needs
Never assume a vendor is secure just because they say so. Ask for documentation, security test results, or independent audits. For critical vendors, those that manage core systems or store large amounts of protected health information (PHI), consider site visits or in-depth assessments before signing a contract.
Always include clear security expectations in your RFPs and contracts.
Once a vendor is onboarded, ongoing monitoring is essential. Security isn’t static, and neither is vendor risk.
Use a combination of checks to stay informed:
- Annual assessments to confirm continued compliance. Standardized questionnaires save time, but dig deeper into high-risk vendors with follow-up reviews or audits.
- Performance metrics that provide insight into how seriously a vendor takes security:
- Time to patch known vulnerabilities
- Completion rates for security awareness training
- Response times during past incidents
- Results from internal audits and how quickly they fixed any is
- Hold periodic business reviews where security is a standing agenda item
- Beyond the technical side, good vendor management includes regular communication. Keep the relationship collaborative, not just transactional.
Share relevant threat intelligence that may help them—and you—stay ahead of emerging risks
- Identify opportunities to improve controls together, especially when systems or processes change
When vendors are treated as long-term partners and held to the same standards as internal teams, your organization becomes more resilient and more compliant.
How Pi Tech Builds Compliance Into Healthcare Software
At Pi Tech, we know that compliance can’t be an afterthought. In healthcare, the stakes are too high, and retrofitting security at the end only leads to delays, unnecessary costs, and potential risks.
That’s why our Specless Engineering methodology weaves compliance directly into every stage of software development, from initial concept to deployment and beyond.
The Pi Way: Compliance by Design
Most development teams treat compliance as a final checkbox. Something to address just before launch. That approach creates problems: last-minute changes, hidden vulnerabilities, and rushed workarounds that don’t hold up under scrutiny.
We do things differently.
With Specless Engineering, we embrace uncertainty without sacrificing regulatory rigor. Instead of locking ourselves into exhaustive requirements upfront, we focus on core objectives and build iteratively, embedding compliance into every loop of the process.
This brings three key advantages:
- Faster Time to Market: By integrating security controls from the beginning, we avoid long remediation cycles. Compliance grows with the software, instead of being tacked on at the end.
- Reduced Compliance Debt: Just like technical debt, compliance debt builds up when regulations are ignored early on. Our approach prevents violations from accumulating and avoids costly rewrites down the line.
- Adaptive Security: Healthcare regulations and threats evolve constantly. Our iterative cycles let us adapt as new rules and risks emerge, so your software stays compliant and secure over time.
Senior-Only Healthcare Expertise
Pi Tech exclusively employs senior developers with in-depth knowledge of the healthcare domain. This expertise manifests in practical ways throughout development:
Our developers understand HIPAA requirements intuitively. They recognize when seemingly innocent features might create compliance issues.
For example, they know that convenient features like "remember me" checkboxes require careful implementation to avoid unauthorized access to PHI.
Experience with healthcare workflows prevents security controls from impeding patient care. Our teams strike a balance between security requirements and clinical realities. They understand when emergency access procedures need to override normal authentication flows.
Regulatory expertise extends beyond HIPAA. Our developers have implemented systems meeting FDA 21 CFR Part 11 requirements, integrated with state prescription drug monitoring programs, and navigated international privacy regulations.
Practical Compliance Implementation
Theory doesn’t protect patient data. Implementation does. That’s why we focus on turning regulatory requirements into secure, functional software.
- We separate PHI from operational data using architectural patterns that reduce exposure and risk
- Our API gateways enforce strict access controls, ensuring that only authorized systems and users access sensitive information
- Automated testing and security scanning are part of every build. We validate encryption, authentication, and audit logging continuously through our CI/CD pipelines
- Code reviews focus on security and compliance, catching risks before they reach production
From architecture and design to deployment and monitoring, we build compliance into the foundation, not as an afterthought, but as part of how we develop healthcare software at every level.
Take Action: Secure Your Healthcare Software Today
Good intentions aren’t enough to protect patient data. Security and compliance in healthcare software demand expertise, disciplined development practices, and a long-term commitment to getting it right. Every day you operate without the proper safeguards increases your risk, financially, legally, and operationally.
Regulations are getting more complex. Threats are evolving faster. And as more systems move to the cloud, the pressure to build secure, compliant software only grows. Traditional development methods aren’t built to handle these challenges. Ours is.
At Pi Tech, we understand the realities of healthcare development. Our senior-only team brings deep experience in compliance, security, and real-world clinical workflows. With our Specless Engineering approach, we build protection in from the start, without slowing down delivery.
Don’t wait for a breach or audit failure to reveal what’s missing.
Partner with Pi Tech to build secure, compliant healthcare software that works in practice, not just on paper.
Contact us today to learn how we can help you move faster while staying protected. Let’s build healthcare technology that puts both patients and privacy first.







